Start / Configure Security - RBAC & MFA
Configure Security - RBAC & MFA
In this step, you will enforce MFA for a DemoUser on AzureAD level to see how easy it is.
After that, you will setup RBAC on the WVD Workspace using multiple AdminUser accounts
We will do this in 2 sections:
- Enable MFA for a demouser
- Configure RBAC on WVD
Enable MFA for a demouser
- Open the Azure Portal from the new Azure AD Tenant, and sign in with the admin account from this tenant (admin@{tenant})
https://portal.azure.com/{tenant}In my example, this would be
https://portal.azure.com/wvdworkshopt01.onmicrosoft.com -
Open Azure Active Directory
-
Click on Users in the menu
-
Click on Multi-Factor Authentication
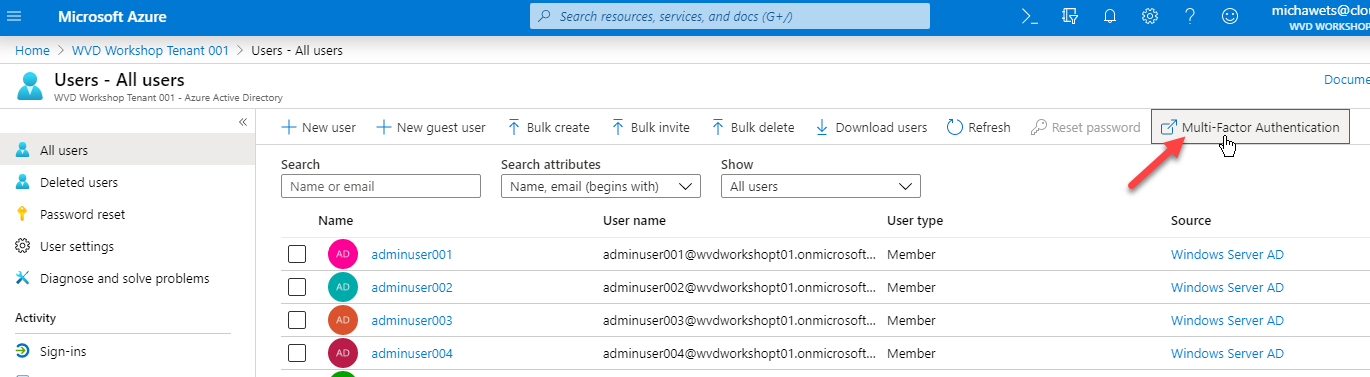
-
Select DemoUser001 from the list and click on enable
Confirm enabling MFA for the user
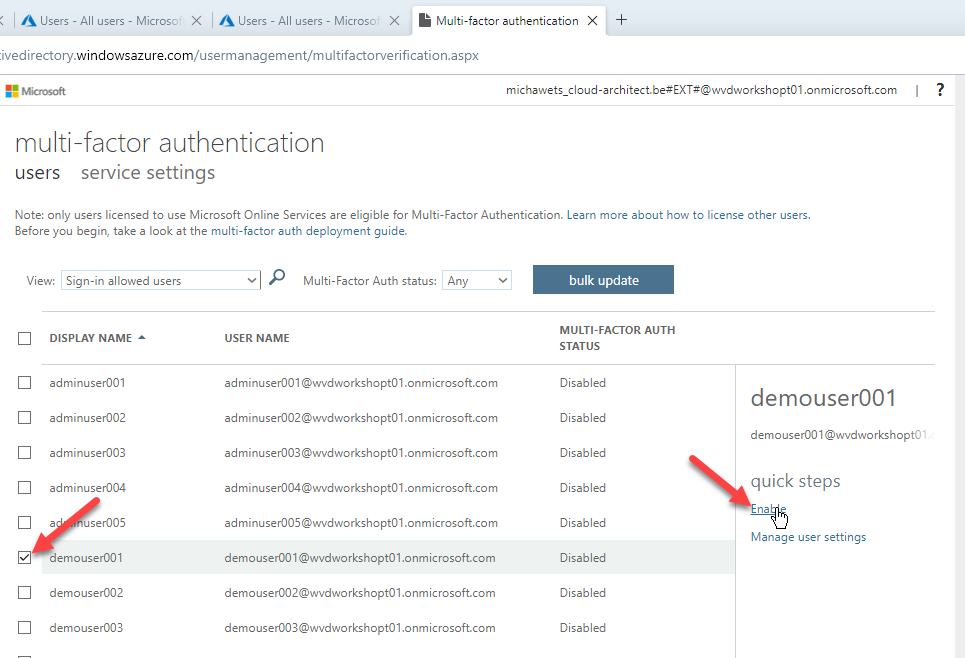
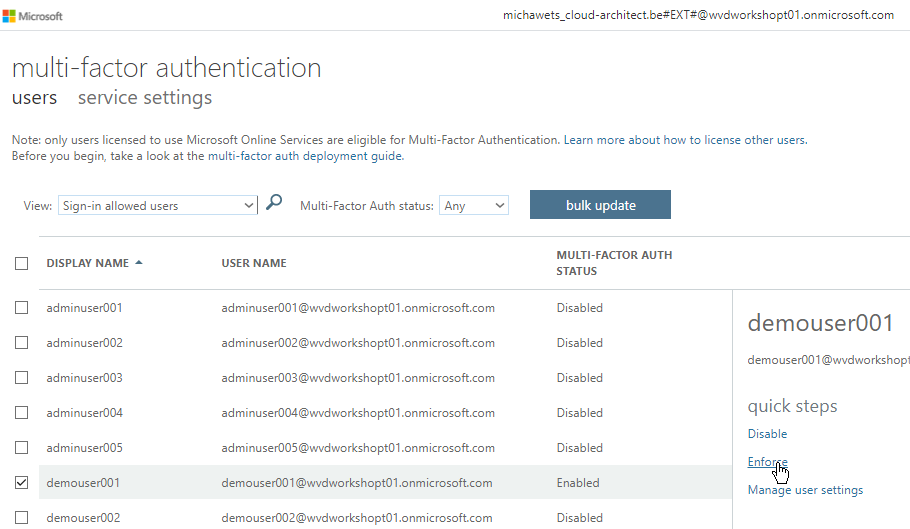
-
Select DemoUser001 again from the list and click on enforce
Confirm enforcing MFA for the user
- Login & try to launch the Full Desktop as DemoUser001 using the HTML5 webclient
You will be guided through the wizard of MFA
Configure RBAC on WVD
We are going to delegate permissions to our AdminUsers.
This is the layout:
| User Account | Level | Permissions |
|---|---|---|
| AdminUser001@wvdworkshopt01.onmicrosoft.com | Resource Group (wvd-workshop-sessionhosts-rg) | Contributor |
| AdminUser002@wvdworkshopt01.onmicrosoft.com | Resource Group (wvd-workshop-sessionhosts-rg) | Reader |
| AdminUser003@wvdworkshopt01.onmicrosoft.com | HostPool ‘wvd-workshop-win10-1909-hp’ | Contributor |
| AdminUser004@wvdworkshopt01.onmicrosoft.com | HostPool ‘wvd-workshop-win10-2004-hp’ | Contributor |
You could do this in the Azure Portal, or by using Powershell.
The steps below will help you doing it in Powershell
-
Launch a Powershell console as Administrator
- Sign in and connect to Azure using the admin account
Connect-AzAccount - If you have multiple subscriptions, and need to change the default subscription, run this cmdlet:
Get-AzSubscription | Out-GridView -PassThru | Select-AzSubscription - Assign the correct roles to the users using this script:
$contributorRole = Get-AzRoleDefinition | Where-Object {$_.Name -eq "contributor"} $readerRole = Get-AzRoleDefinition | Where-Object {$_.Name -eq "reader"} $resourceGroup = Get-AzResourceGroup -Name "wvd-workshop-sessionhosts-rg" $wvdhostpool1909 = Get-AzWvdHostPool -Name "wvd-workshop-win10-1909-hp" -ResourceGroupName $resourceGroup.ResourceGroupName $wvdhostpool2004 = Get-AzWvdHostPool -Name "wvd-workshop-win10-2004-hp" -ResourceGroupName $resourceGroup.ResourceGroupName New-AzRoleAssignment -SignInName "AdminUser001@wvdworkshopt01.onmicrosoft.com" -RoleDefinitionName $contributorRole.Name -Scope $resourceGroup.ResourceId New-AzRoleAssignment -SignInName "AdminUser002@wvdworkshopt01.onmicrosoft.com" -RoleDefinitionName $readerRole.Name -Scope $resourceGroup.ResourceId New-AzRoleAssignment -SignInName "AdminUser003@wvdworkshopt01.onmicrosoft.com" -RoleDefinitionName $contributorRole.Name -Scope $wvdhostpool1909.Id New-AzRoleAssignment -SignInName "AdminUser004@wvdworkshopt01.onmicrosoft.com" -RoleDefinitionName $contributorRole.Name -Scope $wvdhostpool2004.Id -
Sign in into the Azure portal with AdminUser001, 002, 003 & 004 and validate what resources you are able to see.
- You could test even more levels if you want, but this is out of the scope of this workshop