Start / Create Test users and Groups
Create Test users and Groups
In this step, you will
- Create users and groups
- Test synchronisation from Windows AD to Azure AD
IMPORTANT
If this is not a new Azure AD Tenant/Subscription/Windows AD, please make sure that you do not remove/overwrite existing useraccounts or groups
Create users and groups
- Create at least 10 new users & 5 admin users in the Windows AD:
For example:
SamAccountName: DemoUser001
SamAccountName: DemoUser002
SamAccountName: DemoUser003
SamAccountName: DemoUser004
etc
SamAccountName: AdminUser001
SamAccountName: AdminUser002
etc
You can run the following Powershell script in a Powershell console (as Administrator)
$ErrorActionPreference = "Stop" $dc = (Get-ADDomain).DistinguishedName $ouName = "WVD Users" $path = ("OU={0},{1}" -f $ouName, $dc) $ouObject = "" try {$ouObject = Get-ADOrganizationalUnit -Identity $path } catch {} if (($null -eq $ouObject) -or ($ouObject -eq "")) { New-ADOrganizationalUnit -Name $ouName -Path $dc } $username = "demouser" $adminname = "adminuser" $count = 1..10 foreach ($i in $count) { $sam = ("{0}{1:D3}" -f $username, $i) New-AdUser -Name $sam -Path $path -Enabled $True -ChangePasswordAtLogon $false ` -AccountPassword (ConvertTo-SecureString "Micha&BartForProctorsOfTheYear2020" -AsPlainText -force) -PasswordNeverExpires $true -PassThru } $count=1..5 foreach ($i in $count) { $sam = ("{0}{1:D3}" -f $adminname, $i) New-AdUser -Name $sam -Path $path -Enabled $True -ChangePasswordAtLogon $false ` -AccountPassword (ConvertTo-SecureString "Micha&BartForProctorsOfTheYear2020" -AsPlainText -force) -PasswordNeverExpires $true -PassThru } $domainAdminGroup = Get-ADGroup "Domain Admins" $domainAdminGroup | Add-ADGroupMember -Members (Get-ADUser -Filter "name -like 'adminuser*'")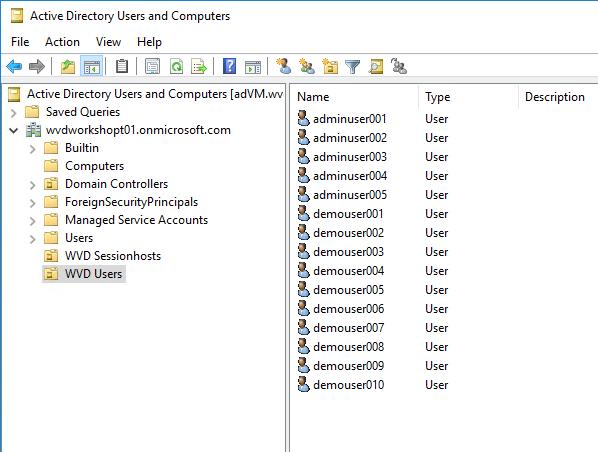
- Create 3 AD Groups for WVD assignments later on
For example:
WVDWorkshopFullDesktopUsers
WVDWorkshopRemoteAppUsers
WVDWorkshopAdmins
Assign “demouser001”,”demouser003”,”demouser004”,”demouser005”,”demouser006” to the WVDWorkshopFullDesktopUsers group
Assign “demouser002”,”demouser007”,”demouser008”,”demouser009”,”demouser010” to the WVDWorkshopRemoteAppUsers group
Assign all adminuser* accounts and your Domain Admin account to the WVDWorkshopAdmins group
You can run the following Powershell script in a Powershell console (as Administrator)
$ErrorActionPreference = "Stop" $dc = (Get-ADDomain).DistinguishedName $ouName = "WVD Groups" $path = ("OU={0},{1}" -f $ouName, $dc) $ouObject = "" try {$ouObject = Get-ADOrganizationalUnit -Identity $path } catch {} if (($null -eq $ouObject) -or ($ouObject -eq "")) { New-ADOrganizationalUnit -Name $ouName -Path $dc } $FullDesktopGroupName = "WVDWorkshopFullDesktopUsers" $RemoteAppGroupName = "WVDWorkshopRemoteAppUsers" $AdminGroupName = "WVDWorkshopAdmins" New-ADGroup -Name $FullDesktopGroupName -DisplayName $FullDesktopGroupName -Path $path -GroupScope Global -GroupCategory Security New-ADGroup -Name $RemoteAppGroupName -DisplayName $RemoteAppGroupName -Path $path -GroupScope Global -GroupCategory Security New-ADGroup -Name $AdminGroupName -DisplayName $AdminGroupName -Path $path -GroupScope Global -GroupCategory Security $FullDesktopGroup = Get-ADGroup $FullDesktopGroupName $RemoteAppGroup = Get-ADGroup $RemoteAppGroupName $AdminGroup = Get-ADGroup $AdminGroupName $FullDesktopGroup | Add-ADGroupMember -Members ("demouser001","demouser003","demouser004","demouser005","demouser006") $RemoteAppGroup | Add-ADGroupMember -Members ("demouser002","demouser007","demouser008","demouser009","demouser010") $AdminGroup | Add-ADGroupMember -Members ("adminuser001","adminuser002","adminuser003","adminuser004","adminuser005",$env:USERNAME)
Test synchronisation from Windows AD to Azure AD
To test the sync from Windows AD to Azure AD, you can exec these steps:
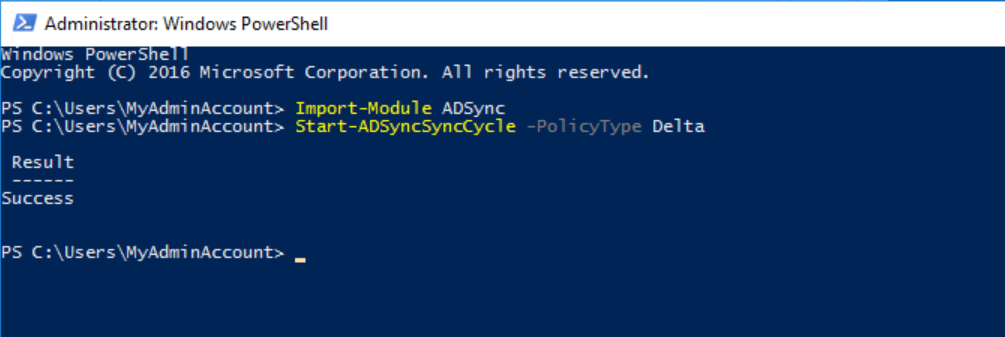
- Force a AD Connect sync
Launch a Powershell console as Administrator
Exec the following cmdlets
Import-Module ADSync Start-ADSyncSyncCycle -PolicyType DeltaNote: If you get an error about the ADSync Module, try
Import-Module “C:\Program Files\Microsoft Azure AD Sync\Bin\ADSync\ADSync.psd1” Start-ADSyncSyncCycle -PolicyType Delta
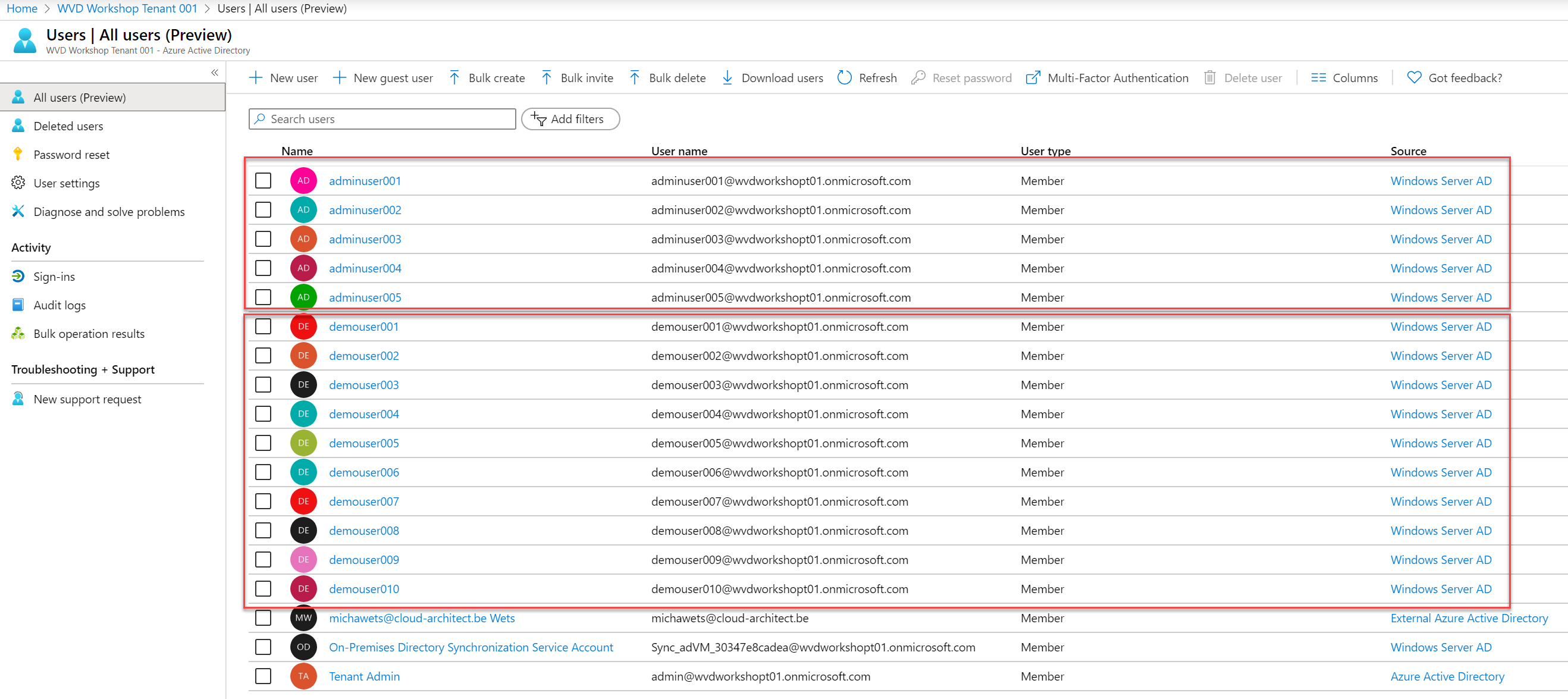
- Open the Azure Portal from the new Azure AD Tenant, and sign in with the admin account from this tenant (admin@{tenant})
https://portal.azure.com/{tenant}In my example, this would be
https://portal.azure.com/wvdworkshopt01.onmicrosoft.com - Check if the DemoUsers appears in the Azure Active Directory users list (could take a few minutes for the sync to finish)